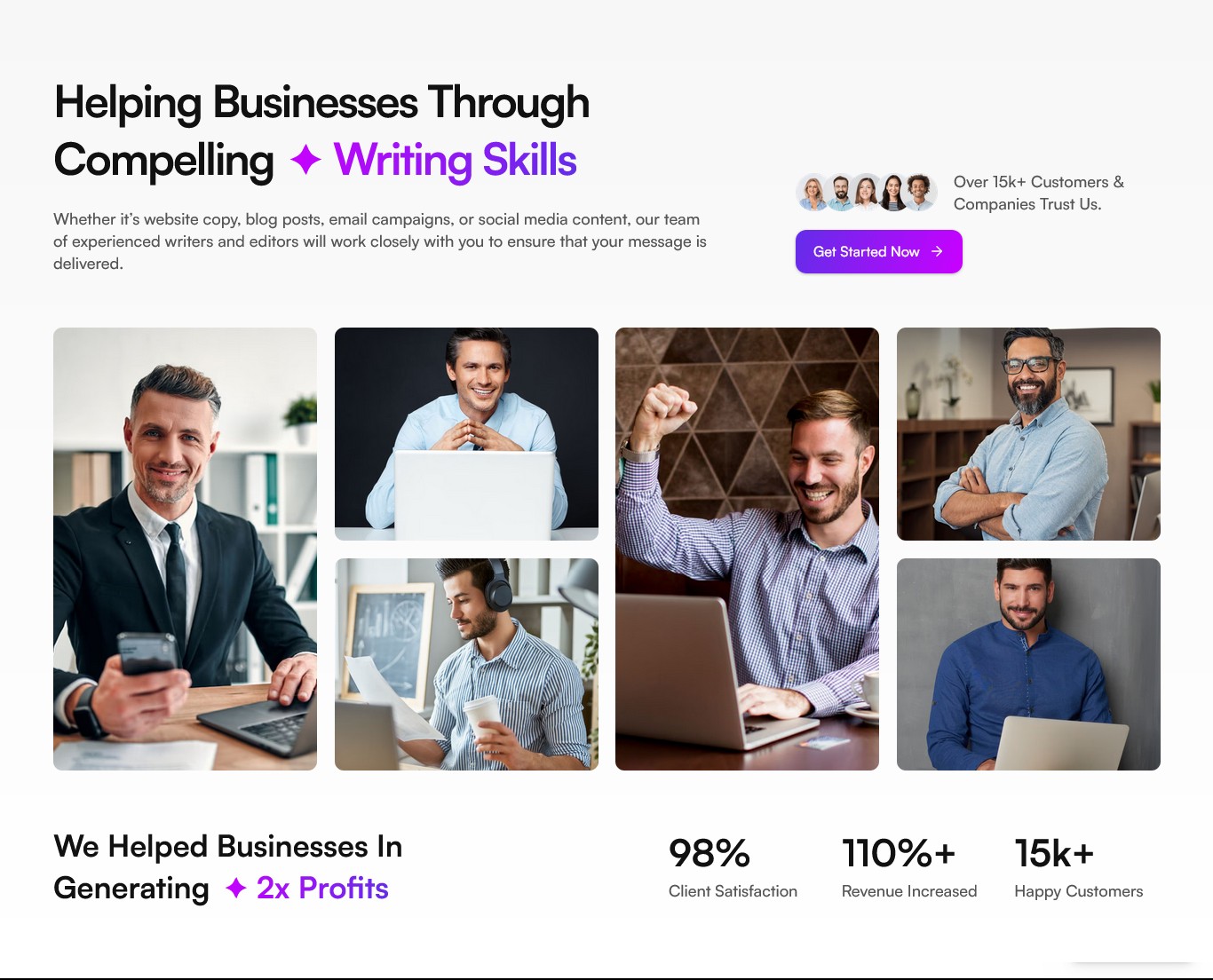
Proactive Protection. Powerful Peace of Mind.



When threats move fast, you need faster protection. Shield delivers aggressive, always-on cybersecurity and IT services. We make sure your team stays sharp, your systems stay safe, and nothing slows your momentum.
Free Cyber Security Webinar
At our cybersecurity agency, we stand as vigilant guardians of your digital assets, offering a comprehensive suite of services.
Free Cyber Security Webinar
At our cybersecurity agency, we stand as vigilant guardians of your digital assets, offering a comprehensive suite of services.
Free Cyber Security Webinar
At our cybersecurity agency, we stand as vigilant guardians of your digital assets, offering a comprehensive suite of services.
Whether you're a small/medium business, medical clinic or a non-profit, our commitment remains unwavering: to empower you with the tools and expertise needed to navigate the complexities of cybersecurity and IT Services with confidence.

Your data, when you need it.
You need your data - it's the lifeblood of your business. We're here to make sure that happens; onsite or remote support, Shield is there for you.

Your data, when you need it.
You need your data - it's the lifeblood of your business. We're here to make sure that happens; onsite or remote support, Shield is there for you.

Your data, when you need it.
You need your data - it's the lifeblood of your business. We're here to make sure that happens; onsite or remote support, Shield is there for you.

Cloud Solutions
Robust and scalable, cloud solutions like Microsoft 365 are not going anywhere. Shield ensures a safe and secure cloud environment for your organization to thrive! From remote access, VoIP, to hosted services!

Cloud Solutions
Robust and scalable, cloud solutions like Microsoft 365 are not going anywhere. Shield ensures a safe and secure cloud environment for your organization to thrive! From remote access, VoIP, to hosted services!

Cloud Solutions
Robust and scalable, cloud solutions like Microsoft 365 are not going anywhere. Shield ensures a safe and secure cloud environment for your organization to thrive! From remote access, VoIP, to hosted services!

Around the Clock Monitoring
You need us, we're here. Cyber criminals don't wait to attack during business hours, so you need security and performance monitoring around the clock. Shield provides the expertise and the attention to detail required to keep your business running.

Around the Clock Monitoring
You need us, we're here. Cyber criminals don't wait to attack during business hours, so you need security and performance monitoring around the clock. Shield provides the expertise and the attention to detail required to keep your business running.

Around the Clock Monitoring
You need us, we're here. Cyber criminals don't wait to attack during business hours, so you need security and performance monitoring around the clock. Shield provides the expertise and the attention to detail required to keep your business running.

Compliance Management
Shield helps businesses meet compliance requirements like PIPEDA, PCI, and more by securing sensitive data, monitoring systems continuously, and providing the documentation and support needed to pass audits and protect against costly violations.

Compliance Management
Shield helps businesses meet compliance requirements like PIPEDA, PCI, and more by securing sensitive data, monitoring systems continuously, and providing the documentation and support needed to pass audits and protect against costly violations.

Compliance Management
Shield helps businesses meet compliance requirements like PIPEDA, PCI, and more by securing sensitive data, monitoring systems continuously, and providing the documentation and support needed to pass audits and protect against costly violations.
Tailored for YOUR business
IT Services
IT Your Way
Extend Your Team

Custom-Fit Solutions
We assess each organization’s goals, risks, and infrastructure to deliver IT and cybersecurity solutions that align with your unique environment—never one-size-fits-all, always purpose-built for impact
IT Services
IT Your Way
Extend Your Team

Custom-Fit Solutions
We assess each organization’s goals, risks, and infrastructure to deliver IT and cybersecurity solutions that align with your unique environment—never one-size-fits-all, always purpose-built for impact
IT Services
IT Your Way
Extend Your Team

Custom-Fit Solutions
We assess each organization’s goals, risks, and infrastructure to deliver IT and cybersecurity solutions that align with your unique environment—never one-size-fits-all, always purpose-built for impact
99%
Customer Satisfaction
99%
Customer Satisfaction
99%
Customer Satisfaction
15 Minutes
Or Less* Response Time
15 Minutes
Or Less* Response Time
15 Minutes
Or Less* Response Time
24 Hour
Monitoring and Endpoint response
24 Hour
Monitoring and Endpoint response
24 Hour
Monitoring and Endpoint response
Monthly
Contracts to ensure your satisfaction
Monthly
Contracts to ensure your satisfaction
Monthly
Contracts to ensure your satisfaction

Firewall and Network Security

Endpoint Protection

Identity & Access Management

Mobile Device Security

Threat Intelligence Services

Security Audits

Data Loss Prevention

Around the Clock Backup
Reviews
Get Started on Your Journey to Dependable IT and Cyber Security Services
Our mission is to empower businesses with tailored solutions that address their needs.
Our mission is to empower businesses with tailored solutions that address their needs.
Our mission is to empower businesses with tailored solutions that address their needs.
24/7 Security Monitoring Constantly monitoring client systems and networks.
Advanced Threat Detection: Utilizing cutting-edge tools and techniques.
In-person and virtual cybersecurity training
Frequently Asked Questions
Frequently Asked Questions
Our expert team combines years of experience with cutting-edge technologies to deliver tailored solutions
Our expert team combines years of experience with cutting-edge technologies to deliver tailored solutions
Do I need to be PCI Compliant?
If you store or handle credit card data in any way - YES! Even if you’re not handling credit card data directly—PCI still expects a few basic steps. We can help you breeze through that SAQ and ensure your setup stays out of deeper compliance scope. That way, you avoid surprises and stay audit-ready.
Do I need to be PCI Compliant?
If you store or handle credit card data in any way - YES! Even if you’re not handling credit card data directly—PCI still expects a few basic steps. We can help you breeze through that SAQ and ensure your setup stays out of deeper compliance scope. That way, you avoid surprises and stay audit-ready.
Do I need to be PCI Compliant?
If you store or handle credit card data in any way - YES! Even if you’re not handling credit card data directly—PCI still expects a few basic steps. We can help you breeze through that SAQ and ensure your setup stays out of deeper compliance scope. That way, you avoid surprises and stay audit-ready.
What geographical regions do you support?
While Shield has offices in Calgary, AB, Winnipeg, MB, and Houston, TX - we support clients accross Canada and the US.
What geographical regions do you support?
While Shield has offices in Calgary, AB, Winnipeg, MB, and Houston, TX - we support clients accross Canada and the US.
What geographical regions do you support?
While Shield has offices in Calgary, AB, Winnipeg, MB, and Houston, TX - we support clients accross Canada and the US.
How can I protect my information online?
To protect yourself against cyber attacks, you should regularly update your software and operating systems, use strong, unique passwords for all accounts.
How can I protect my information online?
To protect yourself against cyber attacks, you should regularly update your software and operating systems, use strong, unique passwords for all accounts.
How can I protect my information online?
To protect yourself against cyber attacks, you should regularly update your software and operating systems, use strong, unique passwords for all accounts.
What is a Vulnerability Assessment, and Why is it Important?
A vulnerability assessment is a systematic process of identifying, quantifying, and prioritizing security vulnerabilities in computer systems.
What is a Vulnerability Assessment, and Why is it Important?
A vulnerability assessment is a systematic process of identifying, quantifying, and prioritizing security vulnerabilities in computer systems.
What is a Vulnerability Assessment, and Why is it Important?
A vulnerability assessment is a systematic process of identifying, quantifying, and prioritizing security vulnerabilities in computer systems.
What is Encryption, and Why is it Important?
Encryption is the process of converting data into a format that is unreadable without the correct decryption key.
What is Encryption, and Why is it Important?
Encryption is the process of converting data into a format that is unreadable without the correct decryption key.
What is Encryption, and Why is it Important?
Encryption is the process of converting data into a format that is unreadable without the correct decryption key.
Unmatched, Custom IT Services and Solutions - 877.321.7374
*SLA times are strictly enforced. See contract for specific details.
Copyright © 2026 - All Rights Reserved
Unmatched, Custom IT Services and Solutions - 877.321.7374
*SLA times are strictly enforced. See contract for specific details.
Copyright © 2026 - All Rights Reserved
Unmatched, Custom IT Services and Solutions - 877.321.7374
*SLA times are strictly enforced. See contract for specific details.
Copyright © 2026 - All Rights Reserved
Get a Cyber Audit!
Get a comprehensive
security report with
remediation steps.
help@shieldnetworks.ca